Overview
The documentation is provided for a general audience of the platform. However there are differences in implementation and nuances unique to every project. This page is simply a check list for the admin, to ensure they have knowlege specific to their system.
Essential Details for access
- Admin Link + Credentials
- FTP Details
- Which folder to upload product images to
- Which folder to upload CMS files to. Like Home page banners etc.
On website updates, some folders are refreshed and replaced. Hence it is important to know which folders you can upload to, to avoid losing data. These folders are used by the developer(s) to supply some base images etc for the website that will always be there on any install. Ideally these can be marked READ-ONLY on the file system by admin to prevent the user from uploading files to them in the first place, but that may not always be the case.
- Understand Dynamic URL parameters for landing pages
- Documentation link
- Link to CPanel (if any)
- Check email address used by ETL process
- Check email address for System generated emails
- Check email address on any emails sent to customer. Check by doing a test order
- Ensure Payment gateway works on all Payment Gateway providers
- Know Image sizes for all content and product pages
- Check images from URL's in Facebook (login via your FB account and use tool) See this
- Check how to use and put UTM codes for campigns See this
- Access to your CDN (if any)
Run through check list
- Run thorugh the ETL process flow to update products and their images
- Run thorugh the ETL process flow to only update product information
- Run thorugh the ETL process flow to only update images
- Update details via Catlog
- Check Catalog Inventory
- If the project uses a CDN learn how to operate and update it + check CDN Admin panel
Project specific Checklist
- Special URL's like International Payment Link, Collections Link etc.
- Special folders where files go and their purpose. Like Catalog, collection banner images, home banner images etc.
- Restrictions when naming files. Example avoid hyphen or delimiter characters in file names that maybe mentioned in the URL itself.
- Know where your organization stores all the product images. You should have a local backup/copy of all your content images and specially product shoot original files. Whats maintained on the web is only optimized version that too for current products on display, older ones maybe deleted to save server Disk Space. Server disk space is more premium and you need to rely on local organizational backups.
Business owners Checklist
When going online, a business owner must be careful about security. We go beyond normal protocol to ensure your site is safe.
Security is not just technical (we do out best technically); but also on your behalf as a business owner. Its like you can have the best security systems, but if you forget to switch the alarm on or leave the door open then you are always vulnerable. The following should help you avoid common mistakes:
- Ensure your corporate identity is not using any particular employee email address but generic ones like info@yoursite.com, customer@yoursite.com. This impacts customer perception and also prevents security faults where an employees account maybe lost, locked or compromized.
- When registering for third party services, avoide using employee specific accounts and names. Use a generic one but not one of your corporate identity. This is because the third party service may spam your email address with their own news letters and marketing material.
- Whenever an employee is leaving, please ensure proper handover and training. We have provided documentation but there are other check-lists mentioned in this document that your employee should maintain and hand over. You should check such check-lists exist in your organization. See the check-lists in previous sections.
- When sharing passwords with vendors or employees of sensitive accounts like DOMAIN, please be sure to change the password once the access is used by them.
- Always ensure you know where all your data and images are. In the event of a disaster, one can always recover very quickly if these are known and up to date.
- Any admin access to website, each user and employee should use their own account handle. Furthermore everyone should change their password first time afer login. This way there is more accountability on anyone making changes.
Finding out what went wrong with a customer
Sometimes, the customer may report a problem that you may not be able to solve and need to escalate. Proper communication of the problem is essential. Please keep the following in mind while escalating an issue:
- Ask or note the date and time the customer experienced the issue. Note, when the customer reports it is not as important as when the customer experienced the issue. Simply based on the time we maybe able to look into our logs and find the exact problem.
- Send a screenshot (if possible), of the issue. Its is preferable to do a COPY/PASTE of the content on the screen rtaher than jsut a screenshot. If its an admin problem you can do this.
- Send the URL / Link of the page with the issue. Copy paste this in TEXT format.
- Ask the client what device and browser they were using at the time the problem occured.
Authorization & Security
The Admin should not share their username or password with anyone. If someone requires access, we can create another account for them with proper defined roles & autohrizatons. This is impostant because all admin logins and changes are audited. The person logged in is accountable for the changes they make to the system and hence identification of the individual who is logged in should be mapped to the real person and not a proxy.
When a person leaves the organization, the persons account should be deleted.
Beyond site Admin Accounts
The rules above should extend beyond the site admin and in general be practiced through an organization (in general). This also implies any email accounts should be in the name of the organization and not an individual.
For example:
customercare@mycompany.com is acceptable, but
tanya@mycompany.com is a bad practice.
You can always setup mail forwards from a particular account to other accounts. For example if all customercare mails have to goto Tanya, then setup a mail forward from customercare to tanya. This also has several other technical and businss advantages, like the email address put in the users address and avoid being marked as SPAM etc.
Similarly, Analytics like Google Analytics accounts should be in the name of the company gogle account. If anyone needs access, then the company can add them via the Google Admin.
Periodic Security Review
The organization should ensure the following:
- All acccounts are checked and any employees or contractors who are no longer required, their access denied from all systems
- Existing employee passwords should be reviewed
- If there is a possible security issue or suspicion, please do not delay in reporting it to the super-admin or developer
- For websites with any sensitive information, ensure atleast your admin module runs on https and not http. You would be required to purchase an SSL certificate for this. It is recommended you buy a higher class SSL certificate that is capable of protecting your website and any sub-domains, but this is not mission critical if all you care is about your website on your core domain.
Periodic Support Tasks (performed by Hosting & Developer)
The people maintaining the site for you perform the following activities from a daily to monthly level, depending on type of project and support plan:
- Daily or Weekly backup of all database content : This means your user data, orders, catalog information is up to date safe based on the peroid
- Heartbeat Services : Check the website is running every 30 minutes (configurable). Note this cannot detect any problems within the website
- Post upgrade Tests: If an upgrade or change is made, then the system is run through a series of basic tests toensure there are no glaring issues. Post any upgrade one must always help the developer test the website for any possible bugs/problems in existing functionality. This happens often and is termed as regression. in the software industry.
Admin Access for non SSL sites
To ensure basic security of admin, even if your website does not use
SSL, we *may* ensure admin pages work on an
https protocol.
SSL costs money if one was to procure a genuine certificate from an issuing authority. Which makes sense if real customers or visitors were sharing personal infromation on yoru website. However for websites that do not have such a need, the admin still needs to be secured. So we employ SSL but we create a
self signed certificate. Meaning, the certificate is not authorized by any 3rd party. In our case thats OK, since for admin internal purpose only you do not need that added verification.
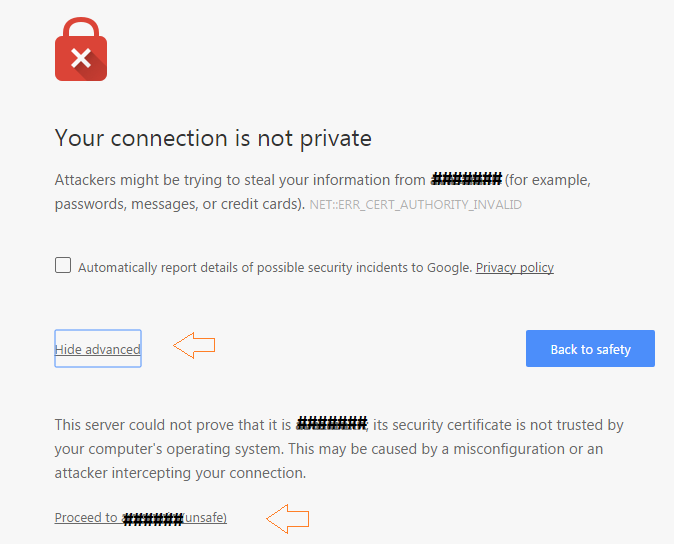
If your site is using a self signed certificate, you maybe prompted with the following type of browser confirmation. Proceed and add the certificate to your browser in the process, so that your browser will not annoy you with the same next time.
The reason why the following screen appears, is because the SSL is telling the browser this is meant to be a secure connection and it technically is. However it lacks the validation from a third party attesting it is genuinely secure. For practical purposes, in this case your data transmission is secure.
Admin Handover
When the admin is changing or handing out, the organization should keep in mind the following:
- All items on this page (check list) are handed to the new person
- Handover training should start atleast 1 week before last day of work
- Inform the developers atleast 1 week before last day of work
- Ensure the list of users who should not have access to the system, is communicated to developer or orgnaization, so their access can be revoked
Miscellaneous Topics
Google Analytics Setup
Setup an Account : Always use an official ID and not a personal ID to login into https://www.google.co.in/analytics/
Setup a Tracking Code : https://support.google.com/analytics/answer/1008080?hl=en ; share this code with us along with the tracking script (in text format).
Add us as a observer, so we can help (Optional) : https://support.google.com/analytics/answer/1009702?hl=en. Our account id to add is neurosys.biz@gmail.com
Google Maps Standard API access
Some projects may use Google Maps. Their maps may need a key to run on the server. Please obtain a ket using your google account by following these instructions.
Site Email and SPAM issues
Sometimes you may feel or your customers may complain that they have not got an email. Please follow this check list to determine the problem:
- Do a bogus or test transaction to check if you or the admin gets an email. Be sure to also check your SPAM folders.
- If no one gets an email then report the issue to the developer.
- If some people get an email and some dont, be sure that the mail is not going in SPAM.
- If the email is going to SPAM folder, then you may want to advise your customers to add your sending email address to their address book. You could display this as a message soon after a user completes some activity that sends an email. Like on a Thank you page after registration or payment.
- If your email is going as spam, additionally you can contact your IT or ask the Hosting company or Admin to add an SPF record to the DNS. An example of an SPF record is
example.com TXT "v=spf1 include:_spf.google.com include:example.com ip4:xx.xx.xxx.xxx ~all"
or example.com TXT "v=spf1 +a +mx include:_spf.google.com include:example.com ip4:xx.xx.xxx.xxx ~all"
...where xx.xx.xxx.xxx is the IPv4 address of the server you want to ensure is recognized as a legit source for emails, in this case example.com.
You can learn more from here.
There is more on SPF records here http://www.openspf.org/FAQ/Common_mistakes and http://www.openspf.org/FAQ/Examples
- Ensure no one else knows any system account information to your mail server. It is important the mail server be protected by a username/password.
Naming best practices
If a name is used to uniquely identify a document or some content or artifact then some special consideration should be given to avoid potential problems.
The reason is that computers use some special symbols that mean special things to them. For example in a URL (link), #, &, ?, =, / have special meanings. A simpler analogy is a file on your computer where "." implies an extension. Example some_file.jpg. One can always call a file some.file.jpg but then this name is prone to hazard as now the computer does not know if the file extension is .file.jpg or just .jpg. Similarly there are other scenarios that we will not get into for now.
Try to follow the below check list when dealing with resource names or names used to identify system content.
- Never start a name with a Symbol
- Use a consistent naming convention for all resources, so the nomenclature is standard. Example: If a resource is named "a_b_c.jpg", then its best to stick with underscores as separators for other names. Little discipline goes a long way in the future.
- The character set should be simple and at most use any or all the following character sets : A-Z, a-z, 0-9, hyphens(-) as delimiters, underscores (_) as delimiters
- The characters to avoid should be: Special characters and any character that cannot be represented in a file name or punctuations that cause confusion like , DOT(.), Comma (,) , #, : , ?, &, tabs or new lines etc.
Data practices
When filling in data please be aware of the following:
- Blank Vs 0 : Lets say you have an Excel sheet with a column called "Sale Price". If you leave it Blank it implies there is no Sale Price for that product. However if you put 0, it means the product could be on sale and be available @ zero unit price. This can have very serious consequences.
- Blank Vs Space(s) : Similar to the above, in certain fields that maybe sensitive, you should be careful nto to have extra white spaces. The human eye may not pick it bute for the computer there could be a difference between a pure Blank (empty) and field and one with spaces.
- Avoid formatting data outside the browser
: Fromatting referrs to applying style over content, like bold , colors, underline etc. Unless you are in a an Admin interface that supports formatting; please DO NOT format data in yoru excel, text, or any other format file. These formattings will be lost or even worse cause some problems when being imported/pasted. This is because formatting is subject to the medium it is being performed on and interportability of formatting is unchartered territory. Additionally, as a general rule it is best to let the software do the formatting for you based on the design and template rather than you manually trying to override it.
Wierd symbols
If you notice some funny looking characters aka symbols, appearing on your screen as part of the name of a product, or title or anywhere in content. For example: ? appearing, where it should be a currency sign like ₹. This is an encoding issue.
Typically an encoding issue creeps in when there is a mismatch or use of characters or letters in the Data/Content from another system that is not web friendly or compatible with the device viewing the characters. The following scenarios will help illustrate how this happens in reality:
Example Scenario Web Page
Lets assume you are using some foreign language symbols in your content. Even if the server is displaying it correctly on your browser. Once published, another computer may not support the required character set. This is similar to using a font that is not safe.
Solution: Ensure the page encoding or the site encoding, supports the required character set you are using or avoid using the characters.
For emails one can see this article.
Example Scenario Systemn Update
Lets assume, you are importing data via Excel in an ETL process. The excel or file, contains some system specific symbols, that are legible on your computer but on loading it into the server. Via the admin panel on your browser you can already see the symbol is getting corrupted. This scenario suggests there is an encoding problem between the File and the Web/System format. This is in other words a data or system encoding issue.
Solution: Ensure the file is saved in UTF-8 format. (default system supported format). If there is a need for another format then that needs to be communicated to development and tested thoroughly.
Example Scenario Email
Unfortunately emails are very restrictive (restricted by the mail client), in how much control we have on rendering them. A good email needs to be safe for all the clients that render it. Here the only real way of ensuring there is no problem is to ensure you use Web Safe characters.
Solution: Use escaped symbols to represent content rather than the symbol.
Page encoding
Page encoding refers to ensuring the page supports characters that are outside the system defined encoding standards. This ideally should not be required as it can result in other inconsistencies across a site, but its more a HACK measure than a solution. In this one ensures the following:
(needs HTML knowledge)
- The HTML page uses appropriate character set and encoding, via the meta http-equiv="Content-Type" content="text/html;charset=ISO-8859-8"> tag. The character set here is just for example.
- If your page uses any non web-safe fonts not supported, then include that via CSS. You can talk to your developer if any other technique is required.
- Use escaped symbols to represent content rather than the symbol.
You can apply the encoding via the CMS in the
page headers. Put the meta tags or any CSS imports in that section.
Site encoding
Similar to page encoding in the way it works, but this applies to the entire website. This is a better way as it ensures consistent handling of characters throughout the website. This should be performed by the developer or you can make these changes in the website template via the Template Editor or raw HTML template files.
System encoding
You need to fix the data in your file/input to use UTF-8 encoding (whatever the system default character set and encoding is). Or talk to your developer if this will be more prevalent across your data.
Host level control
Here is how you have a deeper level of access to the core website files and structure. Before you access or modify any file or setting please be sure to read the following disclaimers also.
Any fault due to changes via CPanel, SSH or any software that operate at a host or an operating system level are not covered under AMC.
Any fault due to changes in core website files which have not been provided by us, are not covered under AMC. To also maintain proper process it is advised (but not mandatory) that changes be uploaded with developers consent.
You can also access files via FTP or File manager, if you have CPanel purchased with your Host plan.
- Webmaster control @ the Host level using CPanel (if CPanel was purchased for your host). These will be shared by developer on request. Root access once shared signifies a high level of responsibility once shared.
- Website files : <home>/public_html/ or / if logging in via FTP user webmaster in FTP. This contains following sub-folders:
- html : All HTML files are in folder
- js : JavaScript files for dynamic UI programming. Currently JS generation is manual but we may move to a tool like TypeScript
- css : CSS files for style control across templates. Please note, CSS generation is a more sophisticated process (using SCSS or other methods depending on project); and if there are any CSS changes they have to go through a development process once you have verified what they are. See SCSS, Susy.
- Within html, template level structure is in templates & dynamictemplates. Any static level HTML is in root and re-usable components are in panels
- All third-party javaScript plugins are in thirdParty.
...Other than the above there are additional folders but they are beyond the scope of regular web and are for backend platform integration.
Backend platform : Stumps is not an open source platform and as per general agreement backend code is not available, however all client web related project files are available as explained above.
- Data: If you are under AMC, data is regularly backed-up (weekly for websites), under <home>/data-backup or / , if logging via FTP user datamaster.
Additionally, via CPanel (if available), you can use PHP My Admin to access the database, perform additional backups, changes, restores. These are all third party software and documentation is available online.
- Read only OS level file rights : By default files are protected as Read-Only @ the Operating System level in many servers to prevent advanced hacking attacks. A process should be followed to change them. Another reason for process is that if mutiple people have different copies of files it can lead to a mess in the update process.
If, you wish to still go ahead and change these (at your own accountability), then you can use the File Manager > Permissions, available in CPanel.